
Unit 42 Log4Shell Compromise Assessment
The complexity of the Log4j vulnerability is still being unraveled as the Java-based logging utility represents another huge broadside to IT and security departments. Watch
Follow the EXOsecure blog to learn about new product features, the latest in security technology, security solutions, and other initiatives.

The complexity of the Log4j vulnerability is still being unraveled as the Java-based logging utility represents another huge broadside to IT and security departments. Watch

Take a deep dive into the malware payload used by one of the Log4j threat actors performing exploitation attempts and see how cybersecurity teams hunt

As security practitioners turn their attention to the Log4j vulnerability, researchers warn remediation will be a marathon, not a sprint. Listen to this webinar hosted

This datasheet highlights how Palo Alto Networks Unit 42 proactively searches for historical and ongoing indicators of compromise to discover previously undetected malicious activity that

This webinar features several Palo Alto Networks Unit 42 strategic advisory security experts in a discussion that walks through critical next steps in communicating your

Meet the Cortex® XDR™: the world’s first extended detection and response platform that gathers and integrates all security data to stop sophisticated attacks. It unifies

Palo Alto Networks continues to successfully address cybersecurity issues by being ready for what’s next. This promo video highlights the company’s willingness to see the

Organizations have more tools, technologies, and processes at their disposal than they know what to do with to combat ransomware. Read this report to gain

Ransomware attacks commanded headlines around the world in 2021 and show no signs of retreating. Read this Unit 42 report for the latest insights on
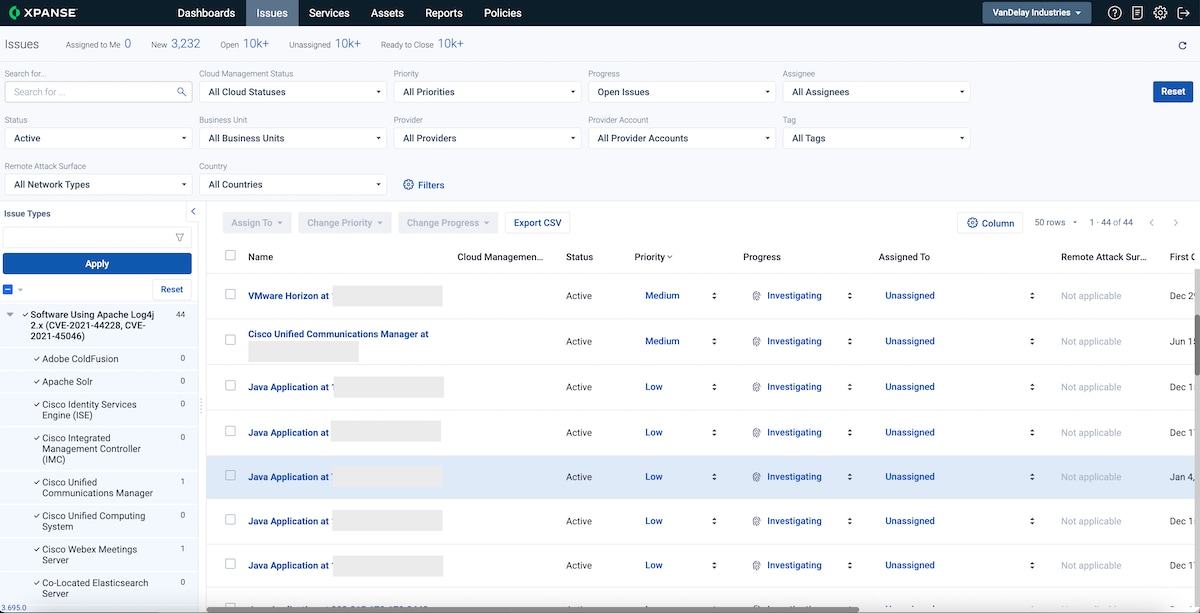
The first step in combating the Log4j vulnerability is identifying applications in your organization that are vulnerable to this developing threat. This blog explains how